Disclaimer: the title of this blog post is inspired by a song by Slayer.
I, being a simple programmer, working for a so-called multinational big enterprise, and deeply involved in programming since ever, have been asked a few times in the recent period some vague questions related to the nature of the Deep Web, or Dark Web as some may call it. The series of questions revealed some deep misconception regarding the nature of the Deep Web, and an intertwined perception of Deep Web and Dark Web, where the latter term is confusingly regarded as an exact synonym of the former. In this blog post, the popular conception of Deep Web, and/or Dark Web, is challenged, in an attempt to clarify the natures of both the Deep Web and the Dark Web, and help the reader better distinguish both types/forms/layers/circuits of the web.
To begin with, in all discussions related to the Dark Web a number of prominent properties are always mentioned:
- the Dark Web is used often by criminals, a statement which is true, the Dark Web is dark by virtue of the fact that it is typically employed for malicious purposes;
- the Dark Web is difficult to reach, which in more technical terms means that it is physically very difficult to gain access the network of criminals, a statement which is, unfortunately and disappointingly, absolutely wrong; and
- communication over the Dark Web is so secure such that no party other than the criminals involved in the network may listen to the connection, another total misconception.
Although the first property of the Dark Web is true, the remaining properties apply only to the Deep Web, as established below.
Deep Web
A normal day in the Deep Web starts by establishing a Virtual Private Network (VPN) connection 12 like a morning prayer! Because otherwise the company’s security is compromised. VPN technology enables the client (the user’s PC, not the user, not the human) to communicate securely with a remote, target server, since communication between two devices over the Internet requires a coordinated work that is accomplished by intermediary devices (servers, routers, switches, and the like) routing the traffic in ways that are opaque to both ends of the virtual circuit, client and server. By establishing a VPN connection, only both ends of the virtual circuit may decrypt encrypted messages transmitted by the other party, while all other nodes in the circuit remain totally agnostic with regard to the content of the encrypted messages. In other words, a message that is sent from one end of the virtual circuit, whether client or server, must traverse the Internet (an unknown number of devices), until the message successfully reaches the other end of the virtual circuit. However, although an intermediary device knows where to forward a message next, the device is (supposedly) incapable of decrypting the message, hence, reading the content of the message3. Therefore, it may be said that the third prominent property of the Dark Web applies to the Deep Web.
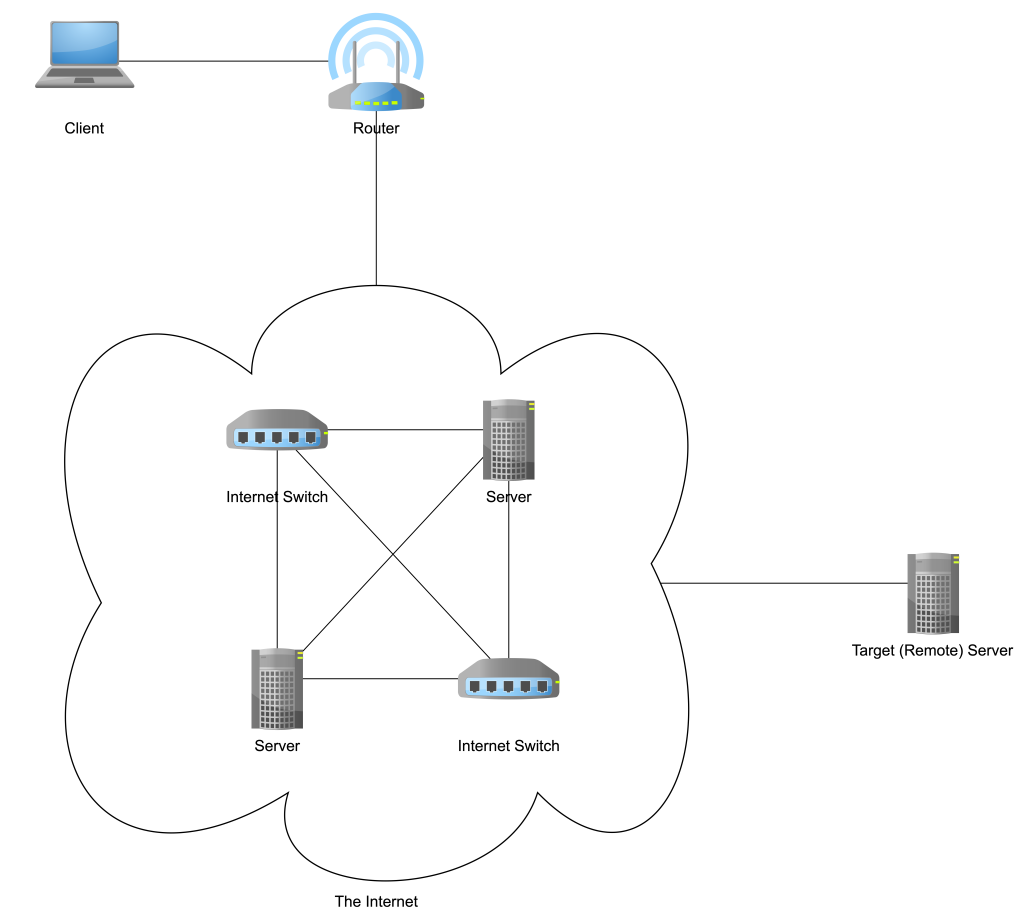
Although a VPN connection may provide a sense of relief at first, a company’s network, which comprises several (hundreds, thousands, or maybe even tens, if not hundreds, of thousands of) devices scattered around the globe, is not yet secure. The target, remote server is usually one that is used for specific purposes, whether development, test, or production (the last term refers to a certain state of a server such that users of a certain system may access the server, the server hosting wikipedia.org for instance is a production server), and one that may not necessarily be associated with a registered domain name (or address for the time being). Remember that if you wish to visit a website, such as Wikipedia, the address of the website, wikipedia.org in this case, must be mentioned in the address bar of your favourite Internet browser. This means that the server associated with wikipedia.org is expected to be a known server on the Internet, and any request made to wikipedia.org must yield a response, Wikipedia’s homepage in this case with address wikipedia.org. However, what if the server does not have a registered name, as our remote, target server? This would make the server a part of the Deep Web, since it is a server that cannot be reached or accessed unless its physical address4 is known beforehand, which is already known by the user operating the client device. Hence, the second condition of the Dark Web is met in our Deep Web.
Note that for a server to remain accessible on the Internet, a certain, unique physical address must be associated with that server. Note also that all addresses are eventually translated to physical addresses (resolved) before proceeding with sending an HTTP request to the server. For demonstration purposes, the following command (works in Windows, Linux, and Mac) causes the client to attempt and resolve the physical address associated with address wikipedia.org. Upon resolution, a number of ping packets are sent to the server, and the server is expected to send a response informing the client that the server is alive.
ping wikipedia.orgNote that upon issuing the command the physical address of wikipedia.org (185.15.59.224 using my computer) is printed in the console:
fadi@Fs-MacBook-Pro ~ % ping wikipedia.org
PING wikipedia.org (185.15.59.224): 56 data bytes
64 bytes from 185.15.59.224: icmp_seq=0 ttl=59 time=9.860 ms
64 bytes from 185.15.59.224: icmp_seq=1 ttl=59 time=13.888 ms
64 bytes from 185.15.59.224: icmp_seq=2 ttl=59 time=11.566 msAlternatively, if you wish to go a bit more Deep Web (not truly though), you may ping Google’s public DNS server as follows:
ping 8.8.8.8the physical address of which is already known, 8.8.8.8. Hence, no resolution is required.
Finally, the kind of data that circulates through a conventional Deep Web circuit owned by an enterprise is corporate data, data that is owned by the company, a fact that opposes the first condition of Dark Web. In other words, the kind of data and/or information that circulates through the Deep Web is legal data, and, in fact, external parties may not in any way listen to, or intervene with, the free circulation of data, not even the government5.
Dark Web
Now that a traditional Deep Web network is introduced, using terminology that programmers do not approve (however chosen for the sake of simplicity), and by illustrating the idea using some vague terms, a figure, and commands that may sound like Codex Regius to the non-programmer, the concept of Dark Web is introduced in this section, and its prominent properties are proven to be pure myth.
With regard to the second property, that the Dark Web is not easily accessible due to physical limitations, it should be noted that criminals do not possess the resources to establish a Deep Web at any scale using their own hardware, and if they had, establishing a network that draws lots of traffic does also attract lots of attention, among which that of security forces and a few criminology enthusiasts. There is no doubt that some criminal networks may not have been identified yet, and that those networks are currently in a functional state, in which case it may be said that an instance of a truly dark and deep web exists. Such a network may remain hidden (deep) as long as the criminals do not attract enough attention, which is bad for business. The moment such a network surfaces, for a reason or another, attempts will be made, for certain, to bring the network offline by any means. One such network is that of firework smugglers in the Netherlands. The firework smuggling business may not sound as thrilling to the reader as organ, drug, or weapon trafficking. However, for a true Dark Web experience, and if you wish to celebrate the New Year’s Eve the very Dutch way, exploring the various communities in WhatsApp in an intelligent manner will eventually lead to firework smugglers. The same way all kinds of traffickers are found. Now, since WhatsApp is easily accessible to every single human being holding a smartphone on this planet, and having a proper GPRS, GSM, G5, or whatever-it-is-called–these-days coverage, labeling such a network as Deep Web contradicts the definition. Alternatively, and which may sound surprising, criminals have made use of easily accessible networks for the purpose of sharing their plans, tweeting publicly for instance, enabling even researchers to listen to their conversations for research purposes6.
In recent years, several encrypted communication networks have been taken offline, hacked, or decrypted by Dutch security forces7 (not mentioning those communication services that have been busted in other countries), making it more difficult for criminals to conduct their malicious activities. Although communication via WhatsApp is (supposedly) end-to-end encrypted, and although HTTPS (the protocol that is unconsciously used to browse the Internet securely by every single human being on the planet) provides a certain layer of security by means of encryption mechanisms, WhatsApp and HTTPS remain some of the most, if not the most, widely used communication channels over the Internet, which raises many questions as why WhatsApp servers haven’t been cracked yet? And why is HTTPS still in use? These questions may hint the reader towards, or the reader may already be, questioning the validity of the end-to-end encryption provided by WhatsApp, or the security of the HTTPS protocol. The question that should have been asked in the first place concerns the liberty that criminals enjoy posting their plans on Twitter publicly! Which makes the situation even more difficult to assess. It should be noted that the aforementioned two communication channels are employed for the purpose of free and secure exchange of information among all humans, unlike the services provided by some other service providers, which attracted a huge amount of criminals, and eventually taken offline. It may be said, therefore, that no instance of Dark Web is truly encrypted. Hence, the third condition is not yet met.
Hackers
Discussing various shapes of the web and data encryption may already have stimulated the idea of a hacker operating somewhere on the network. Although the subject is totally relevant in this discussion, the concept of hacking is not thoroughly discussed in this article. A few examples are discussed, however.
Note that hackers, whether white hat or not, may operate differently, and in more complicated ways. In any case, some hackers do posses their own networks that are truly deep, sometimes so deep due to the fact that they may be decentralised using outdated technologies that are long forgotten. Moreover, their networks may be characterised as being dark as well. You may visit thc.org for instance and gain access to their services free of charge, for no specific reason. If you know your way around the server, you will notice that the guys there are exchanging lists of passwords, for research purposes certainly! Researching your wallet for instance!
Alternatively, for a relatively safe hacking experience, Google Dorks help you hack at a shallow surface some shallow servers. The following Google Dork for instance generates a list of printers that may be accessed through the Internet (just google it up as is):
inurl:printer/main.html
Please do not print nudes or threats. You may instead inform the owner and receive the chance to be titled as a white hat hacker. Back then when I was reckless, I remember printing the results of all 10th grade football matches in Japan, a PDF file that spans several hundred pages, using a printer somewhere on the other side of the planet, which was taken offline a few minutes after fully consuming all the ink cartridges. I wish I could see the owner’s face back then. Now I would like to apologise. If I was smart enough back then, I could have had the chance to see the owner’s face by locating a webcam the owner is expected to encounter. Although locating a certain webcam is extremely difficult, it is still possible to find publicly available, random webcams, and even control the ones at some airport, like I have done in the past, using the following Google Dork:
inurl:/view.shtml
Please be safe out there on the Internet. Please do not act reckless. Maybe a couple of times if you are still young enough to get away with it. If you ever get caught, say you are doing it for research purposes. If I catch you myself, which most probably will never happen, I will show you no mercy! ☺
Notes and References
- Though, I would call it a Virtual Circuit, a personal preference that is the result of studying computing from a hardware perspective, not from a software perspective. ↩︎
- During my career, I made use of Cisco technologies almost exclusively, a company that has been providing since its establishment some controversial service that freaked out Le Monde Diplomatique in one issue. See https://www.monde-diplomatique.fr/2021/07/PERRAGIN/63256. Unfortunately, a fancy subscription, one that allows the subscriber to browse their archive, is required to view the full article. ↩︎
- Similar to the thing that Whatsapp claims to have implemented successfully when you are told when you open Whatsapp sometimes that messages are end-to-end encrypted. ↩︎
- For simplicity, term “physical address” refers to the IP address in this blog post, not the MAC address. ↩︎
- Although this may not sound totally correct, especially to conspiracy theorists, it is the case most of the time. In police-state-like Germany for instance, the last member of RAF to be captured — there is still one member remaining, who was simultaneously number one and number two on Europol’s most wanted list https://eumostwanted.eu/nl/list, recently removed, see https://www.duitslandinstituut.nl/artikel/38660/101-tips-over-raf-trio-op-europol-lijst for more information — was identified with the involuntary help of a couple journalists, since intelligence forces in police-state-like Germany are not allowed to employ certain advanced technologies for the purpose of identifying individuals. See https://www.volkskrant.nl/buitenland/raf-terroriste-wist-dertig-jaar-uit-handen-van-de-politie-te-blijven-ze-werd-gevonden-door-twee-journalisten~b74de467/. A subscription is required to read this article as well. However, in police-state-like Germany, it is still possible to get arrested because you made use of the Torrent protocol, which facilitates communication in the decentralised Torrent network, some form of Deep and Dark Web at once. Please do not attempt to download any illegal content via Torrent during your stay in police-state-like Germany! Note also that no country in the world, not even dictatorial Syria — in a dictatorship, an extensive amount of resources is invested in censorship — has the potential to listen to and analyse all personal communications of its citizens, not mentioning the huge flow of data circulating throw the network. ↩︎
- https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5640454/ ↩︎
- https://www.volkskrant.nl/nieuws-achtergrond/politie-kraakt-versleutelde-app-veel-criminelen-zitten-nu-met-samengeknepen-billen-op-de-bank~b446dfbd/ ↩︎



Recent Comments